In today’s dynamic threat landscape, organizations require structured, adaptable, and measurable approaches to cybersecurity and risk management. Among the many standards and frameworks available, the versatility of NIST CSF stands out as a widely adopted tool, particularly in North America. It provides a comprehensive foundation for building and maturing Governance, Risk, and Compliance (GRC) programs across both IT and OT environments.
The NIST Cybersecurity Framework (CSF) offers several advantages that make it a strong candidate for organizations seeking to enhance their cybersecurity posture:
These features make NIST CSF not just a compliance tool, but a strategic enabler for cybersecurity governance and risk management.

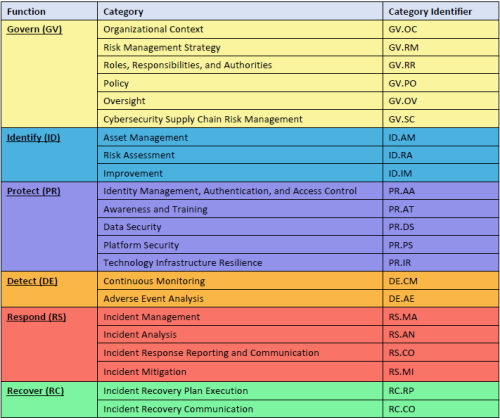
At the heart of the framework are six core functions: Govern, Identify, Protect, Detect, Respond, and Recover. These functions are designed to foster collaboration across teams, support risk-informed decision-making, and promote continuous improvement. Each function is further broken down into categories and subcategories that guide implementation and capabilities assessments.
The Govern function, introduced in CSF 2.0, plays a pivotal role by anchoring the framework in organizational context, risk tolerance, and strategic objectives. This ensures that cybersecurity efforts are aligned with business goals and stakeholder expectations.
To help organizations evaluate their cybersecurity maturity, NIST CSF defines four implementation tiers:
These tiers are not prescriptive capability levels but rather indicators of how well cybersecurity risk is managed and integrated into broader governance processes. They are assessed through two key pillars: Cybersecurity Risk Governance and Risk Management.
Organizations are encouraged to interpret and adapt these tiers based on their unique risk profiles. For example, if a business determines that a critical asset can tolerate 30 minutes of downtime, this tolerance should inform how the organization evaluates its tier alignment. This flexibility is a core strength of the framework—it supports contextual decision-making rather than enforcing a one-size-fits-all model.
To help organizations evaluate their cybersecurity maturity, NIST CSF defines four implementation tiers:
These tiers are not prescriptive capability levels but rather indicators of how well cybersecurity risk is managed and integrated into broader governance processes. They are assessed through two key pillars: Cybersecurity Risk Governance and Risk Management.
Organizations are encouraged to interpret and adapt these tiers based on their unique risk profiles. For example, if a business determines that a critical asset can tolerate 30 minutes of downtime, this tolerance should inform how the organization evaluates its tier alignment. This flexibility is a core strength of the framework—it supports contextual decision-making rather than enforcing a one-size-fits-all model.
One of the most valuable aspects of NIST CSF is its adaptability. Business environments, technologies, and threat landscapes are constantly evolving due to factors such as:
A well-understood and well-documented cybersecurity program enables organizations to respond to these changes with resilience. A framework’s modularity supports iterative improvements and realignment as conditions evolve.
To fully leverage NIST CSF, organizations must embed governance and risk management into their cybersecurity programs. While enterprise-level risk management is ideal, departmental-level assessments can serve as a starting point. However, organizations should be mindful that transitioning to an enterprise-wide view later may require rework if initial assessments lack alignment.
Although NIST CSF originated in the United States, its principles are globally relevant. Cybersecurity challenges transcend borders, and the framework’s structure does not impose geographic limitations. In fact, NIST CSF can serve as a unifying model in environments where both IT and OT environments converge, offering a more integrated approach than frameworks that separate these domains (e.g., ISO/IEC 27001 for IT and ISA/IEC 62443 for OT). Moreover, NIST CSF can be blended with other standards to fill gaps or meet specific regulatory requirements, making it a flexible and future-proof choice.
The NIST CSF is more than a checklist—it’s a strategic tool for building resilient, adaptable, and measurable cybersecurity programs. Its strengths lie in:
The versatility of NIST CSF offers a robust foundation to align cybersecurity initiatives with business objectives, manage risk effectively, and adapt to change with confidence. For more information about NIST CSF, download our presentation NIST CSF v2.0 Overview.
#simpligrc #nistcsf #maturitymodels #cybersecuritycapabilities